Hey there!
If you’re using any of the following Linux distributions, you may want to pay close attention:
- Arch Linux
- Debian
- Red Hat / Fedora
- openSUSE
- Ubuntu
On Septemper 26th, 2024, security researcher Simone Margaritelli reported a series of critical vulnerablities in the Common UNIX Printing System (CUPS).
These vulnerabilities have been assigned the following CVEs:
What is CUPS ?
CUPS is basically a popular printing solution for UNIX-based settings that facilitates communication between programs and printers.
How is CUPS vulnerable ?
Due to insufficient input validation and poor security practices, these vulnerabilities could allow an attacker to execute code without authentication.
However, this risk is only present when a print job is initiated, so if you’re not using CUPS, you’re safe.
How CUPS could be exploited ?
Here’s how the exploit typically works:
- The attacker creates a malicious printer configuration (CVE-2024–47176) using an IPP (Internet Printing Protocol) URL.
- When a print job is initiated, the malicious configuration is triggered, leading to arbitrary command execution (CVE-2024–47177).
- The exploit can use an open UDP port (port 631) to inject malicious code, which will execute during the print process, without needing authentication.
Detection and Mitigation of CUPS exploit
To see if your system is at risk, check the status of the cups-browsed service with:
sudo systemctl status cups-browsed
You can also open the configuration file at /etc/cups/cups-browsed.conf and look for the line:
BrowseRemoteProtocols dnssd cups
If this line is present, your system is vulnerable.
This is the result I got from my system
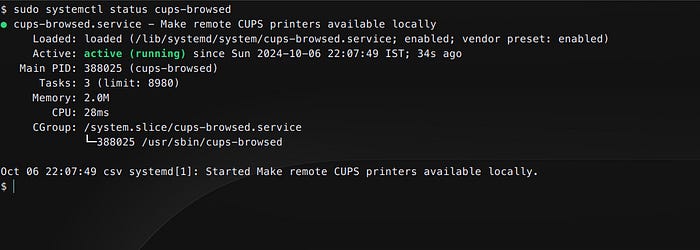
Service running
As you can see, It shows the services is running and is enabled
To mitigate the risk, you can stop and disable the cups-browsed service:
Note: This service is disabled by default in Fedora/Red hat Linux
sudo systemctl stop cup-browsed
sudo systemctl disable cup-browsed
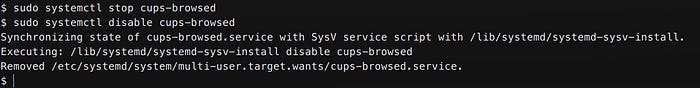
Disabling the service
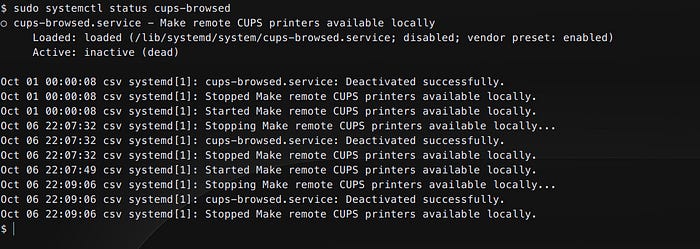
Checking the status again
For further protection, block UDP port 631:
sudo ufw deny 631/udp
The command above will deny incoming requests for the port specified
If you still need to use CUPS, edit the cups-browsed.conf file and change the BrowseRemoteProtocols line to:
BrowseRemoteProtocols none
Then restart the service with:
sudo systemctl restart cup-browsed
Conclusion
At the moment, there are no official patches or updates available from upstream projects or major Linux distributions. Following the steps above can help protect your system until a fix is released.
Thanks for reading, and stay secure!